This is an old revision of the document!
~~REVEAL~~
Workshop 04 - Social Media and Online Safety
What is Online Safety?
The internet is an incredible resource to stay in touch with friends and family, and to connect with products, services and information all around the world.
There are, however, risks associated with being online, such as:
- Scamming and phishing
- Viruses and Malware
- Fraud and Identity Theft
- Gaining unauthorised access to personal/private information
- Cyberstalking
- Cyberbullying
- Hacking
By the end of this session, you will be able to:
- Secure your devices, connection, browser and accounts
- Spot potentially dangerous or risky online situations
- Lock down your privacy settings on social media
Step One - Secure your Devices
On your Desktop/Laptop
The more layers of defence you have, the harder it will be for cyber-criminals to gain access to your computer and its contents.
Some operating systems are more vulnerable to attack than others. Windows tends to be less secure than Mac and Linux, for example.
Only install reputable software. If something is free or seems too good to be true, do your research and make sure you’re not accidentally downloading spyware or malware.
Use secure passwords to lock your device when not in use. Consider using a setting that locks the device after a set amount of time if not in use.
Don’t leave your device unlocked and unattended in public areas, even for a short time. Even if it’s locked, someone can still steal it if it’s left alone.
Always keep your software up to date, as this will include security patches which help to reduce vulnerabilities. This includes your operating system, browsers, programs, plugins, etc.

Install a firewall. A firewall acts like a barrier between your computer and any authorised programs trying to access it. If there are any attempts to access your system, it will tell you so that you can either authorise or deny access.
Install anti-virus software to protect against unauthorised software that can attack and compromise your system. Examples of viruses and malware (malicious software) include:
- Keyloggers (records your keystrokes)
- Ransomware (holds your system or details hostage in demand of payment)
- Worms (causes harm and self-replicate to spread to other computers/devices)
- Trojan Horses (software that misleads the user about its true intent)
- Rootkits (designed to provide unauthorised access to a system)
And more.
Install anti-spyware if it isn’t already included in your anti-virus software. Spyware is a type of software that collects information from you without your approval, which is then passed back to a third-party website. It is often difficult to remove by yourself.

On your mobile
Use a secure password, pin, gesture or biometric data to lock your device when not in use. Consider using a setting that locks the device after a set amount of time if not in use.

Keep your device’s software up to date, as security patches help prevent or repair vulnerabilities. This includes the IOS, apps, etc.

Only download reputable apps from trusted sources, such as Google Play and the iPhone App Store.
Install reputable security software that includes anti-virus and potentially anti loss/theft capabilities.

Keep Bluetooth turned off or set it to hidden if not in use.

Consider using an app-lock application to require a pin or other verification before opening particular apps, so that if people do get past the lock-screen, they’ll still have an added layer of security to get through before accessing sensitive information.

Consider enabling remote locking and wiping functions on your device, if supported. If something happens to your device, this will allow you to lock your phone or wipe it, even if it’s not in your possession.
Consider using auto-wiping functions. iPhones, for example, have a setting you can enable to automatically wipe the device if the pin is entered incorrectly a set number of times.

Don’t leave your device unlocked and unattended in public areas, even for a short time. Treat it as you would your wallet – never let it out of your sight. Also be very cautious of lending it to people, even if they seem harmless, and never let them out of your sight if you do. Handing over your unlocked phone can leave you vulnerable.

Consider including emergency information as a picture on your lock screen. If you do misplace your device, this may help get it returned. You can include contact details for a trusted friend, for example.
Step Two - Secure your Internet Connection
Setting up your home Wifi
Your internet connection allows your computer (and other connected devices) to communicate to the outside world. If your connection is not secure, it may allow others to access your computer and personal information, or to use your connection without your permission for whatever purpose.
Change the administrator password from the default on your router. Default passwords for many routers are available easily online. Choose a strong and secure password to replace it. (This screen will look different, depending on your router)

Disable remote router management. If people can access your router remotely, it makes it easier for others to make unauthorised changes – especially if you’ve kept the default administrator password!
Use strong encryption. WPA2 is the strongest encryption protocol currently provided. If your router was produced before 2006, it will not have this option, and it will be more vulnerable than newer models. (This screen will look different, depending on your router)
Give your SSID (Service Set Identifier) a unique but non-identifying name. E.g. ‘Wifi art thou Romeo’ rather than ‘Billion7800N’ (default router name makes it easier to find default login details, for example) or ’John Doe at 123 Fake Street’ (personally identifying information)
Set a strong password as your Network Key. This is not the same as your administrator password (to edit the router settings) – this is the password people will use to gain access to your wifi network. If you want to revoke access once you’ve given that password to someone, you’ll need to either change your SSID or Network Key.

Turn off Guest Networks that don’t require a login. Only give access to people you can trust to use your network responsibly.
Activate your router’s firewall if it isn’t turned on by default.
Keep your router firmware up to date. Some routers will let you check this with a button directly on the router – others will require you to log into the device to check.
Consider using a VPN. VPN stands for Virtual Private Network, and acts as a tunnel between your computer and the internet through a third party server. It is an added layer of protection against potential prying eyes.
Consider physical access. Someone with quick physical access to your router may be able to pair a device with it quickly by pressing a button if Wifi Potected Setup (WPS) is enabled. Consider disabling WPS or only allowing access to the physical router to people you trust.
Using Public Wifi

Free wifi is useful, but it does come with security risks. It pays to be safe when using public wifi options.
- Only use public wifi offered by networks you know and trust. Eg, the State Library wifi. Avoid obviously dodgy networks – eg, an open network with the name ‘Free Wifi’. Verify the network with staff before connecting, if you have to
- Opt for password protected public wifi if possible, over fully open networks. E.g. some places will only give passwords if you’re buying a coffee, rather than giving access to everyone all the time
- If the network presents terms of service and privacy notices, read them. There can be important information about how they use your data, what kind of content is restricted, etc.
- Avoid working with sensitive data if using public wifi, such as logging into secure sites, online shopping, sending personal emails with identifying data, doing internet banking, etc. If you must do something with sensitive data over a public network, make sure you’re using a secure site to do so
- Make sure you have secured your device as mentioned in the previous steps. E.g. make sure you have anti-virus and firewall software installed
- Identify the network as a public network when you connect, if connecting via computer. Turn off file sharing, and consider turning off location services also
- Turn off wifi when not in use.
- Consider avoiding public wifi altogether. Tether your mobile phone to set up your own mobile hot-spot if you need to use the internet on other devices (like your laptop). Setting up a mobile hotspot with your device will differ depending on your model (and Android vs Apple), but guides are easy to find online if needed.
Interesting viewing: 7 year old hacks into public wifi network in just over 10 minutes. https://youtu.be/qQVCHt5S9B0
Step Three - Secure your Browsing
Different Browsers offer different levels of security. It is a good idea to check the security and privacy settings, so you know what information is being shared. Sometimes these settings are under the ‘advanced’ options.

Note some of the content options below.

Some software features that provide functionality to a web browser may also introduce vulnerabilities. You can turn these off completely, or in some browsers, turn them on only sometimes.
Cookies are files placed on your system to store data for websites. They can contain any information that a website wants to store. Eg, the sites you visit, or login to access the site. They can only be read by the website that made the cookie.
Cookies can be a privacy concern, as they can track visitor information. If intercepted, it can give attackers the information contained in the cookie – e.g. login credentials
Java is a programming language used to develop active content for websites. Java applets usually execute within a “sandbox” (interaction with the rest of your system is limited).
There are potential vulnerabilities that could allow it to ignore these restrictions. Signed Java applets can also ignore sandbox restrictions, but users often need to authorise them before they load
JavaScript is a scripting language used to make websites interactive. There are specifications in the JavaScript standard that restrict features such as accessing local files
ActiveX is used by Microsoft Internet Explorer to allow the browser to use other applications. It can be quite vulnerable to attack VBScript is a scripting language also unique to Internet Explorer. These are not used often. Use them only if you need to
It is up to you to decide what to allow, and what to restrict, along with other content settings, such as allowing access to camera, microphone, location, etc.
- Check for 'HTTPS:' in website addresses. Don’t enter sensitive information into any site that doesn’t use it.
- 'HTTPS:' indicates that the site has a SSL (Secure Socket Connection) Certificate installed.
- SSL encrypts the traffic between you and the website, so that other people can't see your information.
Ensure you’re happy with your privacy and security settings.
Be careful when you install browser plugins and extensions. Some may introduce vulnerabilities, so do you research first.
Always keep your browser up to date. Updates often include security patches to reduce vulnerabilities.
Only enter information into sites with 'https:'
Step Four- Secure your Accounts
Passwords are the first line of defense to secure your accounts – they should be something only you know.
Cyber-criminals can crack your passwords, if given the chance:
- Specialist software can use a brute-force attack to test hundreds of letter, number and symbol combinations very quickly, much faster than any human
- A dictionary based attack will cycle through common words used as passwords
- Guesses can be made based on personal information they know about you
Also give consideration to your username. E.g. ‘admin’ is a very easy username to guess if you’re the administrator of a website!
How to pick a password
Do:
- Use numbers, upper case and lower case letters, and symbols
- Create something you’ll be able to easily remember
- Create a long password – at least 8 characters (except where the site won't let you)
Don’t:
- Use common words/phrases
- Use words or numbers that could be easy to guess (e.g. your dog's name, your birthday)
- Repeated characters or predictable combinations (eg, 1234)
Easy method of password generation
- Think of a sentence you can easily recall
- Use a part of each word (e.g. 2 or 3 letters from each)
- Use numbers and symbols instead of letters. Use some capitals too.
E.g.:
- Sentence: ‘ilove interiordesign’.
- Sentence fragments: ilointrdsgn
- Substitution and capitalisation: !lo1nTRdsgN
Other example passwords:
- I ate six sundaes = 186SunD@e5
- May the force be with you = Mt4bw1thU
- Herbs are the best = herRtb3sT
Try doing it in a different language – it can make it even more difficult to crack!
Password Security
Make your passwords different
Don’t use the same password and password/username combinations across all accounts. Use different passwords when possible.
This can be easy! You can put extra letters in your password to make them different. E.g.
- Gmail Password: 18GIL6SunD@e5
- Facebook Password: FOK186SunD@e5
- Twitter Password: 186SunD@e5TW
Be careful
- Try not to use your passwords on public networks, or on public computers
- Don’t ‘save’ passwords on computers unless you are the only user.
- Always log out after using accounts in public places (e.g. on work computers)
- Don’t enter your passwords through links in unsolicited emails or phone-calls - they might be a scam. Always go directly to the site or call the company if you are not sure.
- Don’t enter passwords on non-secure sites (ones that don't use 'https:')
- Don't share your passwords with others
- If you need to keep a record of your passwords, write them down and hide them. Don't keep passwords in emails or on a file called ‘passwords’ on your computer.
- You can use a password manager. If someone else uses your password manager though, they will have all your passwords
- Use Two Factor Authentication if you can
What if your account is used by someone else?
If you think your account has been used by someone else, change your password/s immediately and/or perform a password recovery. If you use the same passwords across other sites, change all.
Password recovery
When you set up a password, you may also be asked to provide a secret question and answer set to be used for password recovery. Common examples include:
- What is your mother’s maiden name?
- What was the first street you grew up on?
- What was the name of your first pet?
Use information only you can know (You can even use fake information, if you can remember it!). If your password is strong, but your password recovery is weak, you ca still be hacked - especially if a cyber-criminal can access to your email account.
Using 2FA
2FA stands for Two Factor Authentication – a type of Multi Factor Authentication. Many sites and services only use one verification method to confirm your identity:
E.g. a Username/Password Combination
Two Factor Authentication adds another layer of security by using at least two pieces of evidence that you are who you say you are. For example:
- something you know (e.g. a pin, a password, or answers to a secret question)
- something you have (e.g. a bank card, security token, your mobile phone to receive a pin via text message or push notification)
- something you are (e.g. biometric data - a fingerprint scan, retina scan or voice recognition)
This can make identity theft harder for a cyber-criminal. It can make your accounts and transactions more secure if you use more than one way to confirm your identity.
Eg. This website sends a token via Push Notification

You must enter the code that shows up on your phone to make the transaction

It is a good idea to use Two Factor Authentication if you can.
2FA is not perfect – especially on mobile phones.
- Security tokens sent by push notifications (from an app) are more secure than SMS. SMS can be intercepted
- If you don't have your phone, if it is not charged, or you don't have access to the internet/network, you can not access your accounts that use phone 2FA
- Your phone could be lost or stolen. You might keep your email and other accounts logged in on your phone. If someone steals your phone, they could gain access to your email, other accounts, and access to your 2FA method
Two Factor Authentication reduces your risk. It makes it harder for a cyber-criminal to attack your accounts. But it is not 100% perfect.
Spotting Scams and Staying Safe
Many people are tricked with internet scams every day. Scams trick people into giving personal details and secure information (such as login credentials) that can lead to identity fraud. Scams might trick people into giving credit card details and money.
Stay safe by being careful online.
If you think something might be a scam, be safe, and check https://www.scamwatch.gov.au. The site has a long list of common scams.
ACCC Example Video: https://www.youtube.com/watch?v=BL7WJM342Uc
The most important things are:
- Be aware that scams exist
- Keep your personal data personal
- Know who you’re dealing with, and know who to trust
- Keep an eye out for fakes (emails, phone calls, websites, etc)
- Don’t click on anything you don’t trust (website links, email attachments, etc.)
- Be careful if someone asks you for money, personal information, or account details
- It is better to be safe than sorry
We’re going to look at some of the most common scams and how to spot them. There are many more.
Phone Scams
- Always be wary of text messages and calls from numbers you don’t recognise
- When possible, try to keep your mobile phone number a secret or only known by legitimate businesses who have secure privacy policies
- Even if your number seems private, scammers can still use random number generators to contact your number
Missed Call Scams are when a scammer calls your phone, but only a short time, so it shows a missed call.
- Calls are often from international numbers, and may appear as missed calls multiple times.
- If you call back, you get charged a high rate – much more than a standard call.
- They might try to keep you talking for a longer time to charge you more.
To avoid this type of scam:
- Don’t return calls to numbers you don’t recognise – especially if the number is from overseas
- Don’t return calls to numbers that start with 1900 or 19 (these indicate premium line numbers in Australia)
- Block problematic numbers if they keep calling
If you do fall victim to this type of scam, contact your mobile provider. Sometimes, they will remove the charges for you
Premium Service Text Scams are when a scammer sending you an unsolicited text message that tricks you into replying. If you reply, you will be charged a premium text rate.
- These are often disguised as customer surveys, or competitions, such as answering trivia. This is so you reply more (so they can charge you more.)
- If you do reply, you may also be signed up to a premium services that you don’t know about until you see your next bill.
To avoid this type of scam:
- Be careful of unsolicited text messages, especially ones that offer prizes. Do not respond to numbers you don’t recognise
- Do not respond to any number starting with 1900 or 19 (these indicate premium line numbers in Australia)
If you do fall victim to this type of scam
- Contact your mobile provider. In some cases, they will remove the charges for you or unsubscribe you from this service
Remote Access Scams (a common type of phishing) is when a scammer calls you and claims to be from a technical support service. They tell you that you have a phone or internet problem, and try to get you to hand over personal information, provide login credentials or credit card details to pay for a ‘fix’ the problem.
To avoid this type of scam:
- Never give an unsolicited caller access to your computer
- Never give your personal, credit card or online account details over the phone unless you made the call or it’s from a trusted number
- If you receive an unsolicited call claiming that they need remote access to fix a problem, hang up. Real companies like Telstra or Microsoft will not do this.
If you do fall victim to this type of scam
- If you have given access to your computer or think it may have been hacked, seek help from a qualified computer technician.
- If you think you have provided your account details, contact your bank or financial institution immediately and change credentials as soon as possible
Phishing
Phishing scams are when scammers try to trick you into giving personal information like bank account numbers, passwords and credit card numbers.
Personally identifying information can be used in identity fraud, so always be careful before giving your passport information, licence number, tax file number, medicare number, or other details.
You could get an email, text or phone call pretending to be from a bank, telephone company, tax office or other business, asking you to update or verify your details. They could ask you to give information quickly to secure your account.
They are often designed to scare you – e.g. they could pretend to be from Centrelink and tell you to confirm your details or risk stopping your payment.
To avoid this type of scam:
- Never click on links or attachments in emails claiming to be from banks or organisations asking you to verify your details or log in using their link. (If you search for the exact words in the email online, you may find that it is a known scam).
- Check emails against ones you know are real. Do they follow the same format? (Eg, The real ones may use your full name, to prove they are official.) Emails should not have formatting errors, or incorrect grammar and spelling. If in doubt, check it out!
- Check the email address. Is it from the real organisation? Does it come from a different domain name, or follow a different structure than usual? E.g. NetBankNotification@commmbank.com instead of NetBankNotification@cba.com.au ?
Check website addresses carefully before entering login credentials or other personal information, especially if you didn’t type in the website address yourself.
- Is it secure (uses 'https:')?
- Is it different from normal – e.g. commmbank.com instead of commbank.com.au?
- Never provide your personal, credit card or online account details if you receive a call claiming to be from your bank, ATO, Centerlink or any other organisation. Instead, ask for their name and extension number. You can call the organisation directly (using their official listed number) to check
If you do fall victim to this type of scam, change your account details immediately, and contact your bank, financial institutions or other agencies immediately to secure your details.
Buying and Selling Online
Be careful when buying from classifieds without seeing the item in person first. Scammers might use information from real ads to trick you, then tell you that you can’t see the item before paying. Eg, they might say they are traveling or have moved overseas, and will deliver once payment has cleared.
- Check reviews for the seller before buying
- Use a payment method with fraud protection (e.g. don’t pay by money order, wire transfer or international money transfer – try paypal payment instead)
- If something seems too good to be true, it might be a scam. Eg, rental properties and underpriced big ticket items that ask for payment upfront
- Be careful when selling on classifieds – especially the buyer wants to pay with a cheque, or want an expensive item (like a car) without seeing it in person
- The scammer might 'overpay' via cheque, then get you to refund the difference. When the fake cheque is refused by the bank, the scammer will have both the item and the ‘overpayment’ you refunded
- Never send items until payments have cleared
Be careful when buying from unknown online stores, especially if they are new social media stores. It is quick and easy for scammers to create a fake store online. ACCC Example Video: https://www.youtube.com/watch?v=3IIuT4Jo4f8
- If prices are too good to be true, it might be a scam. Sometimes you won’t receive goods at all – sometimes you will receive goods, but they are not genuine
- Check for online reviews of the store from trusted sources and real shoppers
- Check for privacy policies, terms and conditions, and policies about refunds and return. Do they comply with local laws?
- If they don’t accept payment methods that include fraud protection, don’t buy. If they’re asking for credit card details, is the payment gateway they’re using trusted and secure?
- Does the online store have a way to contact them via methods other than email? Eg, do they have a physical address and telephone listed? If they do list those details, are they legitimate?
If you do fall victim to this type of scam and you have used a legitimate payment method with fraud protection (such as credit card or paypal), you may be able to arrange a charge-back.
You may also want to contact your local Consumer Protection Agency. In Queensland, that is the Office of Fair Trading: https://www.qld.gov.au/law/fair-trading
Online Social Interactions
Socialising online comes with its own set of dangers – especially when it comes to people you’ve never met in real life. It can be tempting to think that you ‘know’ someone after chatting to them for a while, or reading what they’ve sent you. It always pays to be safe.
ACCC example video: https://youtu.be/YDt0F7ETmRU
‘Catfishing’ is the practice of setting up a fake profile to take advantage of people often looking for romantic partners. Catfish profiles are usually set up on dating sites, but can also use social media
- The scammer may show signs of developing strong feelings for you in a very short space of time. They will try to make you trust them quickly. Always be careful if this happens
- Consider doing a 'reverse image search' – catfish scammers often use pictures that belong to other people to build up a ‘real’ looking profile.
- Never send gifts, money or personal details to someone you don’t know in person. Usually the scammer will try to make you feel for them to send these things. Eg, they have a sick relative, or they want to fly to meet you.
If a friend or family member has an account (email, social media, etc) hacked, similar methods can also be used.
- Sometimes the hacker might message people on social media (eg, by using Facebook Messenger) to tell them that they’re traveling in another country and have no money to get home
- Because it seems to come from someone we trust, it seems real
- Confirm the facts with them using a different method – e.g. by telephoning. Be careful if they ask to have money transferred to them by untraceable means – e.g. money order, international transfer, etc.
- If in doubt, say no
Where to go for more help
There are many more scams than the ones we’ve listed here. It pays to be vigilant against cyber criminals. https://www.scamwatch.gov.au/ provides a comprehensive list of many scams.
If you suspect you’ve been scammed, the Australian Competition and Consumer Commission has resources on how to get additional help here: https://www.scamwatch.gov.au/get-help/where-to-get-help
- Banking - Your bank or financial institution
- Cybercrime - Australian Cybercrime Online Reporting Network
- Financial and investment scams - Australian Securities and Investments Commission
- Fraud and theft - Your local police - call 131 444
- Spam - Australian Communications and Media Authority
- Tax related scams - Australian Taxation Office
- Identity Fraud - iDcare. iDcare is a free government-funded service which will work with you to develop a specific response plan to your situation and support you through the process. Visit the iDcare website ( https://www.idcare.org/ ) or call 1300 IDCARE (432273)
What is Online Privacy?
Online privacy involves the ability to control what information you show about yourself over the internet, and to control who can see that information.
Some information you give on purpose. Eg, If you set up an account that requires a name, address, phone-number, etc. This is Personally Identifying Information.
Other information you might not know you’re sharing – Eg, shopping habits, online search history, or sites you have visited. Most of this information is Non-Personally Identifying Information – it is connected to 'someone’, but it could not be used to identify 'you' personally.
Who Owns your Data?
Video explaining who owns your data: https://www.youtube.com/watch?v=y1txYjoSQQc (up to 1.46 minutes is most relevant)
Information may be about you, but it is not owned by you. It belongs to whoever collects the data.
- It is important be aware of terms and conditions and privacy policies before deciding to use a service. For a quick check of some common website conditions - check https://tosdr.org/
- Your data can be used for advertising, or for making ‘targeted content’. On Facebook, it even changes when posts are shown to you
- Often we give our data to get a service. E.g. if you use Facebook, you give them permission to use your data, so you can connect with friends and family. Facebook profits by ‘selling’ data to advertisers, to make Facebook ads
How to secure your data
- Be careful about how much information you share online.
- Information such as telephone numbers, your name, address, photos and location tagging can be used to identify you. Your date of birth is often used in Two Factor Authentication to access accounts - eg, banking institutions – so don’t tell everyone
- Secure your browsing – firewall, anti-virus, vpn, only logging into sites with https:, etc.
- Check your privacy settings and make them as secure as you can
- Consider if you want to allow cookies. Cookies can track information like the sites you've visited. You can turn off cookies in your browser settings, but you may lose other website functionality
- Consider archiving or deleting data and accounts you no longer need. The less information you make available, the less there is to compromise
The only way to be sure your data is truly secure is not to give it in the first place. This is becoming increasingly difficult though as services become more connected.
Is information you put online (especially on social media) ever really private?
Once you put something on the internet, there is no guarantee that it will stay private. Even with the most secure privacy settings, there are still ways people can obtain what you’ve put up.
- People who do have access can take screen-shots and show people who don’t
- People who do have access may copy or download your pictures/information and show people who don’t
- You may inadvertently give access to someone with malicious intent (eg, by allowing another app to use your information)
- There may be a security flaw that makes private information public (even login credentials)
The easiest way to keep private information private is not to share it on the internet.
Never have an expectation of complete privacy when you put something online.
Do not put anything on the internet that you would be ashamed for someone you care for to see.
How To Set Your Social Media Privacy Settings
There are many social media channels you may want to use. Each one will have its own terms of service, which identifies how your data is used, stored and transmitted. Most will have a specific page set up to explain how privacy works on that platform.
Today, we’re going to focus on the three most commonly used social media platforms:
- Facebook
- Instagram
- Twitter
As with email and telephone, you can be scammed on social media. Always be careful.
- Don't click links you are unsure of - especially shortened URLs that hide the real site address.
- Be very sure that people sending friend requests are who they say they are. It is easy to set up fake profiles.
- Be careful of memes that ask you to reveal your birthdate or other identifying details. Some are disguised as quizzes or 'name generators' that trick you into revealing personally identifying information to the public.
Facebook offers a number of settings to control your privacy on an account level. These help you decide who sees what you post and how people can connect with you.
You can adjust these on the ‘Settings’ page:

Timeline and tagging settings allow you to restrict who can see what you share, and who can ‘tag’ you in a post. You can make lists to show content to specific groups of people (eg, below, I have created specific lists for ‘people to see photos’)

The ‘Review what other people see on your timeline’ option can be very helpful, as it allows you to view your timeline as a general internet user, or even a specific person.

How to create friend lists
You can create friend lists to share content only with specific people. To do this, go to the Facebook home page, and on the left-hand side, you’ll see the Friends lists option.

Select ‘create new list’ from the options at the top of the screen.

Give your list a name, and add people. You can now use that list when changing your privacy settings.

Setting privacy on individual posts
You can set privacy levels on individual posts. You can use a list, default settings, or exclude just certain people.
Select the privacy setting you want from the drop-down menu. It will stay on this setting by default the next time you post, but you can always change it back.

If you made a mistake, or you’ve changed your mind, you can change the privacy of a post later, too.

Anyone can do this with their posts. Your comment on someone’s post takes the privacy settings of the original post.
Eg, if it was ‘Friends’ (visible to only their friends) and then changed to ‘public’, your comment will also be visible to the public too.
Facebook Pages and most Facebook groups set all post to ‘Public’. If you comment, be prepared to have it seen by everyone. Your account level privacy does not protect your content from being seen if you post in on something marked as public.

Blocking allows you to block activity – you can access this under ‘settings’. If someone is harassing you or bullying you online, it may be a good idea to block them completely. You can also report bad behaviour on individual posts.

Facial recognition may be something you want to turn off to maintain your privacy to some degree.
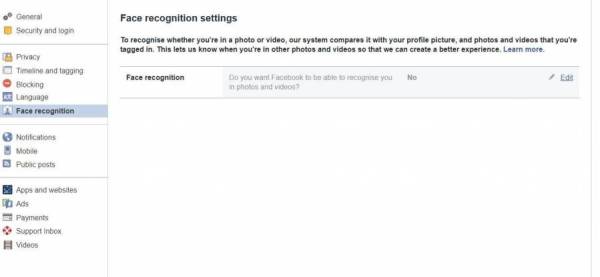
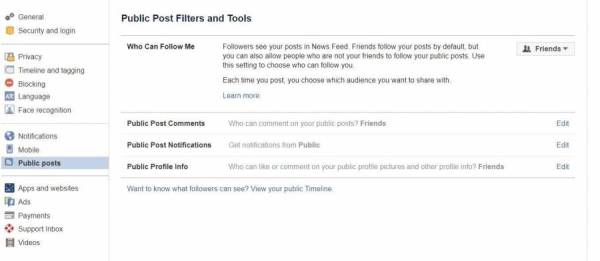
Some posts are set to public by default – eg, your profile picture, and cover pictures. These settings allow you to adjust who can comment on and follow your public information.
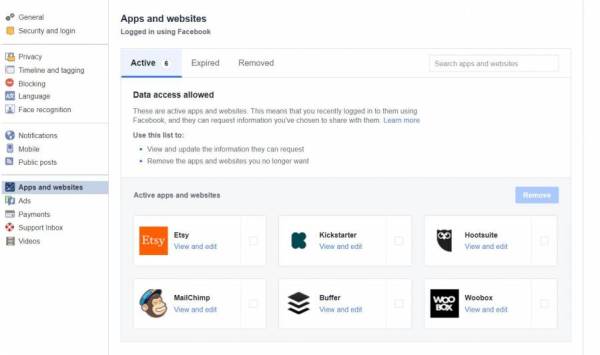
View and edit the accounts you’ve logged into using Facebook. By logging in using your Facebook profile, you are allowing those sites to access certain information. It is a good idea to regularly check if you are still happy with that information being shared.
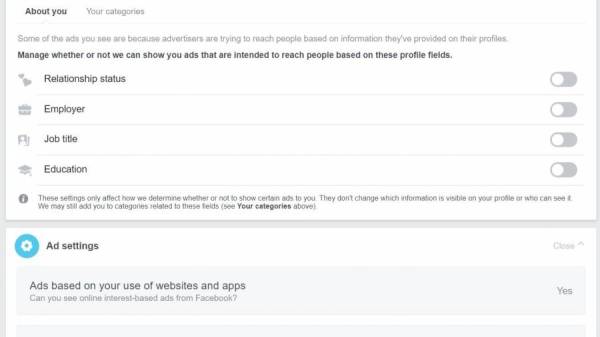
The next item on the privacy list is ‘Ads’. Advertisers use the data Facebook collects to show you advertising it thinks you will like.
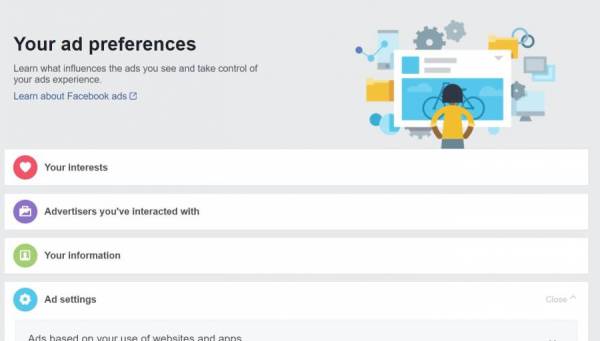
A lot of your data is here. Eg:
- Companies who have uploaded your contact information to advertise to you
- What types of ads it shows you based on your interests.
You can remove information from these sections (e.g. your interests), but even if you do, Facebook will continue collecting data and rebuilding those lists.
You can change permissions in this section to allow or deny advertiser access to certain information.
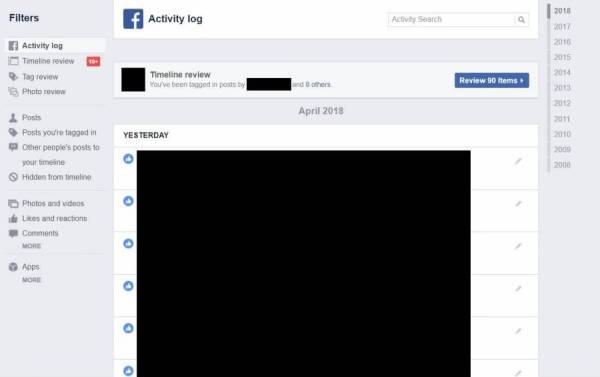
Regularly check your activity log and review your data. Do you still need to share all that information? You can remove what you don't need.
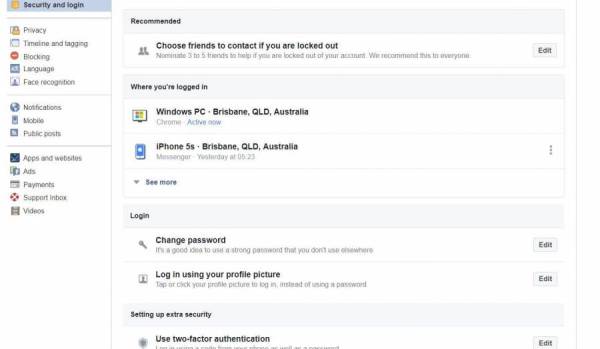
You can turn on Two Factor Authentication or other security log-in settings. You can nominate people to vouch for you if you get locked out of your account.
The security and log-in screen is also where you can review if you’re logged in on other devices, and log out remotely. If you left it logged in somewhere accidentally, you should log out here.
There is a lot to consider when it comes to privacy on Facebook. Just remember:
- Check your settings (and retained data) regularly
- Assume that nothing is private. You never know who can see what you post
- Be very careful with post permissions. Remember that people can change them after the fact
- Report and block people who are harassing or bullying you online
If you’re not happy giving so much of your data, consider not using Facebook
Instagram is owned by Facebook, so it has similar levels of targeting and data-retention. It is a good idea to review their privacy policy in a web browser rather than on your phone, as it may be easier to read and review. https://help.instagram.com/155833707900388
Review your privacy settings by accessing your settings from your profile screen. The ‘gear’ symbol is what you need to click.

Your options may look different depending on your account type. If you have a personal account, you will have the option to set your profile to private:
- If your posts are set to public, anyone will be able to see your profile and pictures. If you want to prevent individual people from commenting or liking posts, you can block them
- If your posts are set to private, your photos will be visible to people logged into Instagram who you've approved to follow you
- If you share a private post on other social media, people outside of Instagram will be able to see your post (just not on Instagram)
You can turn off commenting on individual posts by click the three little dots beside the post information (…) and selecting, ‘Turn Off Comments’.

Remove or report individual offensive or insulting comments by swiping right on a comment and selecting the appropriate action.

You can set up two factor authentication for your account under the ‘two factor authentication’ tab.

Access your Twitter privacy settings from your profile menu.

Once on the Settings and privacy page, you can see your privacy and security options. You can set up two factor authentication and set basic settings. On the left, you’ll be able to review more extensive privacy, security and account settings.

Privacy and Safety gives you a broad overview – you can turn on and off options as you wish. If you want only those who follow you to see your tweets, for example, pick ‘Protect your tweets’. If you don’t want to show your location when you tweet, leave ‘tweet with your location’ unchecked.

If someone is harassing you or bullying you on Twitter, you may want to block them completely. Add them to your block list if you do.

You may give access to apps to connect to your Twitter account.Eg, so you can post to Twitter from Instagram. Check these regularly, and take away access if you no longer use the apps.

We'll also look at the ‘Your Twitter Data’ tab. You will have to provide your password again if you want to access this section, as it holds sensitive information pertaining to your accounts.
From here, you can review the information Twitter retains about you. You can also request the list of advertisers who are targeting you and request that all of your Twitter data gets emailed to you in a file.

Remember, even with tight privacy settings, you still can’t stop someone seeing a screen over someone’s shoulder, or taking a screenshot to show other people.
Always play it safe, and never post anything you’re not happy with the whole world seeing.
Play The Game
Let's check our email address to see if it has ever been compromised, we'll use the website https://haveibeenpwned.com/


